The pharmaceutical sector, a critical node in the global healthcare infrastructure, is becoming increasingly reliant on digital technologies for everything from R&D to supply chain management and direct patient care.
This dependency exposes the industry to heightened cybersecurity risks that could compromise sensitive data, disrupt manufacturing processes, and, ultimately, impact public health. In this view, robust cybersecurity goes beyond compliance needs and becomes a critical business continuity element.
The risks are magnified by the sector’s unique vulnerabilities: extensive intellectual property, vast stores of personal health information, and a complex network of global suppliers. A breach in this environment does not just result in financial losses – it can delay the production of life-saving drugs, erode public trust, invite severe regulatory scrutiny, and even become a public health concern.
Thus, securing digital assets becomes synonymous with protecting human life and emphasizes the need for an advanced, proactive cybersecurity strategy that adapts to the expanding and evolving threat landscape.
Our client, a leading pharmaceutical company, faced a daunting challenge—a significant data breach that exposed sensitive research data to unknown threats.
This breach not only threatened competitive advantage but also risked severe regulatory penalties and loss of patient trust. In an industry where confidentiality and data integrity are paramount, the implications of such vulnerabilities are profound and hard-hitting.
Moreover, with drug counterfeiting on the rise, the validity of the currently available data is questioned, introducing doubt and confusion in the supply chains. This can, at best, lead to widespread product recalls and, at worst, put your customer’s life at risk.
How, then, can a company in an industry as critical as pharma can recover from a breach?
To add fuel to the fire, the investigation into the breach was hampered by limited system access and significant communication barriers across departments.
These obstacles underlined the need for a more integrated approach to cybersecurity, where technology and human processes align seamlessly to preempt threats.
With Surg’s assistance, the client worked on formulating a new cybersecurity strategy that is closely aligned with its community objectives and corporate strategy.
We employed a two-pronged approach for this:
To address the preexisting vulnerabilities, we initiated a comprehensive security assessment across the Microsoft Stack. This assessment identified critical misconfigurations that, once addressed, can lead to better detection, response, and overall posture.
Next, a detailed action plan was developed, specifying the location and nature of the misconfigurations and the steps required for rectification.
Our active and expedited approach to the problem led to a quick and efficient implementation of the solutions. We also helped the client’s team upskill effectively to productively manage new protocols.




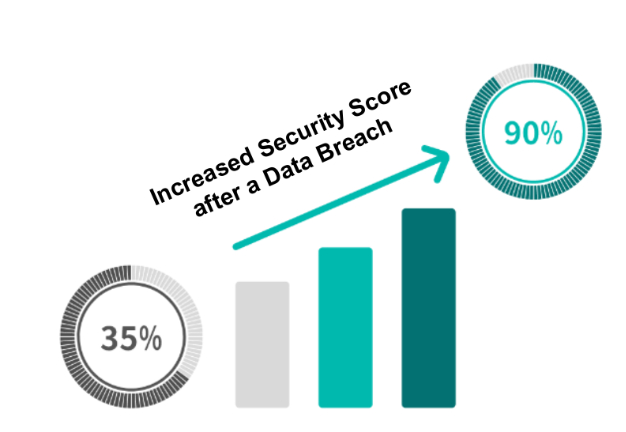
Post-implementation, the client’s security score improved dramatically, taking a jump from 35% to a whopping 90%.
This numerical leap signified more than just a benchmark; it was reflective of the reduction of the attack surface and improved detection and response posture.
Sometimes, all it takes to establish a resilient security infrastructure is the right set of tools, paired with the right talent and best practices.
Get in touch with SurgSecure now to explore our tailored security solutions and take the first step towards a safer, more resilient business.

501 5th Avenue I New York,
NY 10017